In the ever-evolving landscape of cybersecurity, where threats are growing in sophistication and frequency, enterprises must adopt a proactive approach to protect their critical assets.
This proactive stance involves implementing robust security measures that address the most common vulnerabilities and attack vectors.
In this article, we will delve into two fundamental pillars of enterprise security: Multi-Factor Authentication (MFA) and Zero Standing Privileges (ZSP).
We will also explore how WhiteSwan is leading the charge in fortifying enterprise defenses by emphasizing the importance of MFA everywhere and securing against unsecured Remote Desktop Protocol (RDP) access.
White Swan’s approach to enhancing enterprise security aligns with the industry’s best practices, as highlighted in the Sophos report on modern cybersecurity challenges.
Compromised Credentials Are a Persistent Threat
The digital age has brought immense convenience but has also introduced significant security challenges. One of the most persistent and insidious threats enterprises face is the compromise of user credentials.
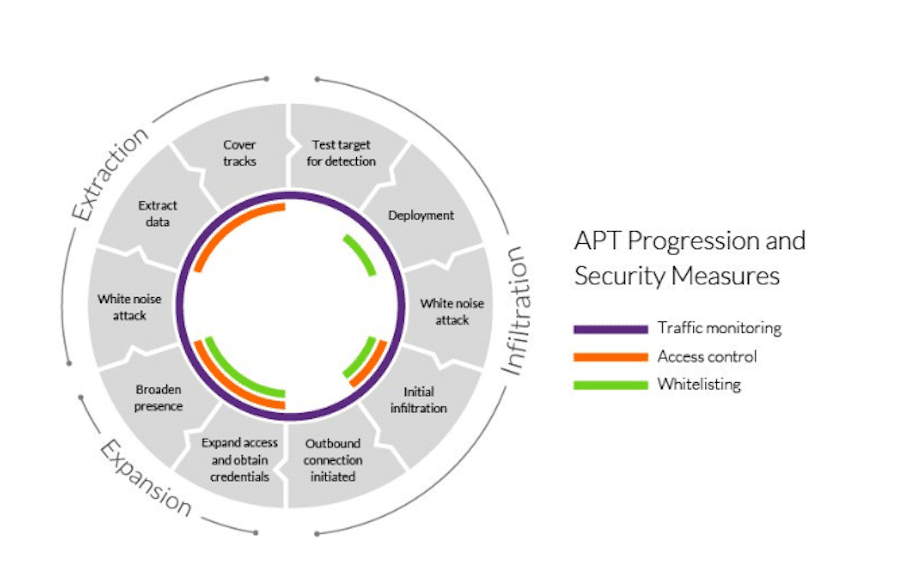
Cybercriminals are relentless in pursuing these valuable pieces of information, whether through phishing attacks, brute force attempts, or social engineering tactics.
Once they possess valid credentials, attackers can infiltrate an organization’s network, often with disastrous consequences.
Imagine a scenario where an unsuspecting employee falls victim to a phishing email. The attacker gains access to the employee’s username and password, which grants them entry into the corporate network.
From here, the attacker can move laterally, escalating privileges and potentially wreaking havoc within the organization. It’s a sobering reality that organizations must confront—the first line of defense, username and password, is alarmingly vulnerable.
MFA Is Essential
Enter Multi-Factor Authentication (MFA), the beacon of hope in the battle against compromised credentials. MFA adds a layer of security by requiring users to provide two or more verification forms before gaining access to an account or system.
This typically involves something the user knows (like a password) and something they have (like a mobile device or smart card).
Even if an attacker manages to steal a user’s password, they would still be thwarted by the need for the second authentication factor.
MFA offers a robust defense against unauthorized access and significantly raises the bar for cybercriminals attempting to breach an organization’s security.
It’s not merely a convenience; it’s an imperative security measure that should be implemented throughout an organization’s infrastructure, from email accounts to critical systems.
Reduced Dwell Time
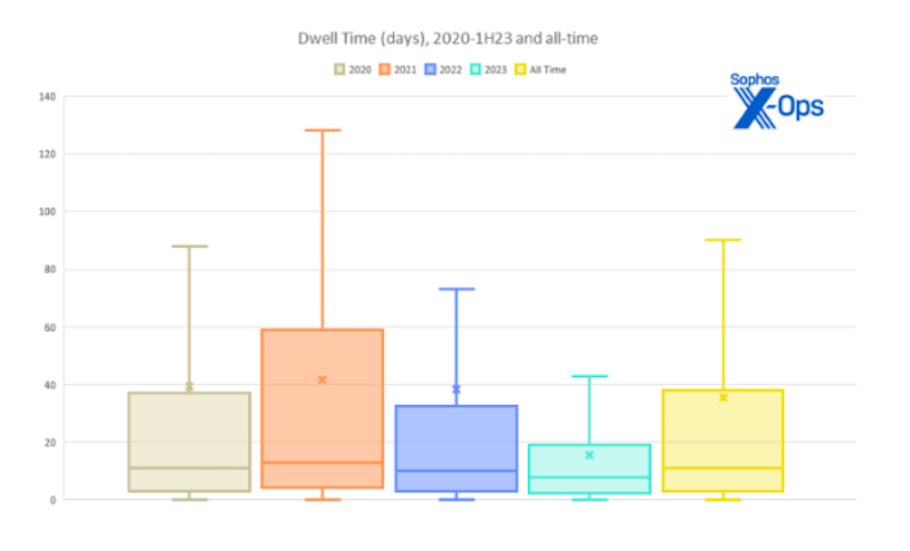
The cybersecurity landscape is dynamic, with new threats emerging every day. As a result, the window of opportunity for attackers has grown smaller.
Dwell time, the duration between a breach occurring and its detection, has steadily decreased.
This reduction is a double-edged sword—it means that attackers have less time to exfiltrate data or cause damage, but it also means that organizations must detect and respond to threats faster than ever before.
In this fast-paced environment, MFA plays a pivotal role. By ensuring that attackers face an additional authentication hurdle even with stolen credentials, MFA contributes to faster threat detection.
Any anomalous login attempts or access requests can trigger alerts, enabling security teams to react swiftly and mitigate potential damage.
Continuous Attack Activity
Cybercriminals operate around the clock and do not adhere to business hours. They are constantly probing and testing organizations for weaknesses. This continuous attack activity means that security must be a 24/7 endeavor.
A breach can occur at anytime, and organizations must be prepared to respond promptly.
This is where the importance of continuous monitoring and response readiness becomes evident. Security solutions should be equipped to detect threats in real time, regardless of when they occur.
Additionally, responding rapidly to emerging threats is crucial in preventing them from escalating into major security incidents.
Active Directory Servers as a Target
Active Directory (AD) servers hold a position of paramount importance within an organization’s IT infrastructure. AD serves as the cornerstone for user authentication, authorization, and management. Consequently, it is an attractive target for cybercriminals.
If an attacker gains control over AD, they essentially hold the keys to the kingdom, with the ability to manipulate user privileges and access throughout the network.
To secure an organization effectively, protecting AD servers is non-negotiable. The breach of these servers can have catastrophic consequences, and organizations must prioritize their security to prevent such incidents.
RDP Risks
Remote Desktop Protocol (RDP) is a valuable tool for remote access to servers and workstations.
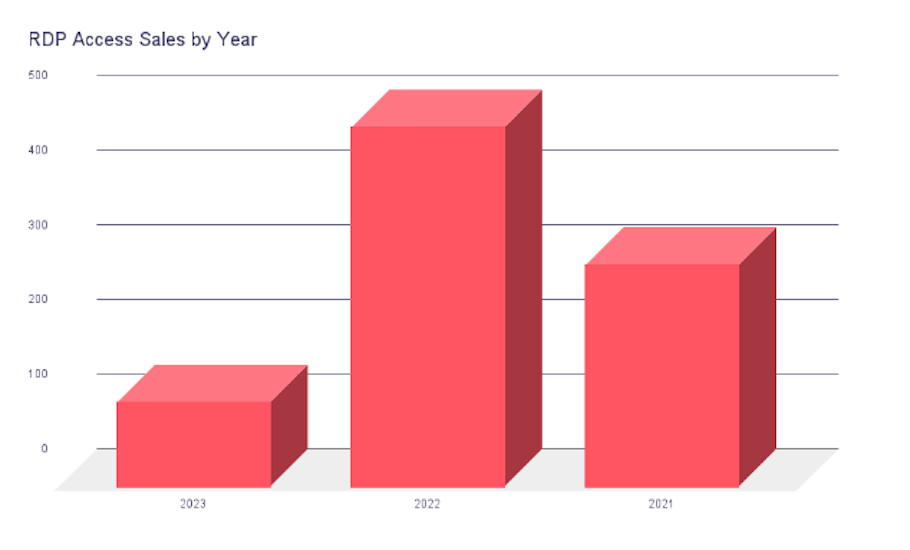
However, it is not without its risks. Attackers often exploit vulnerabilities in RDP to gain unauthorized access to systems. Once inside, they can use RDP to move laterally within the network, escalating privileges and causing significant harm.
RDP is particularly susceptible to attacks because it is a common entry point for cybercriminals. To mitigate these risks, organizations must take steps to secure RDP connections and ensure that unauthorized access is prevented.
The Importance of Telemetry
Comprehensive telemetry data is the lifeblood of effective threat detection and response. Telemetry involves collecting data from various sources within an organization’s IT environment.
This data provides valuable insights into user behavior, system performance, and potential security threats.
Access to robust telemetry data is akin to having a radar system that can detect threats on the horizon. It enables organizations to identify suspicious activities, anomalies, or potential breaches in real-time.
When properly analyzed and correlated, telemetry data empowers security teams to respond swiftly and decisively to emerging threats.
How Whiteswan Addresses These Challenges
Whiteswan, a leading name in the realm of cybersecurity, recognizes the gravity of these security challenges. It has taken proactive steps to address them, providing enterprises with a comprehensive solution emphasizing the importance of MFA everywhere and securing against unsecured RDP access.
MFA Anywhere: Granular Security Without Compromising Directory Systems
One of Whiteswan’s standout features is its MFA Anywhere capability. This innovative approach to Multi-Factor Authentication ensures granular security without interfering with directory systems.
Unlike traditional MFA solutions that are often invasive and in line with directory systems, Whiteswan’s MFA Anywhere operates at the most granular level.
This means users can enjoy Multi-Factor Authentication’s benefits without disrupting their workflow.
MFA can be seamlessly integrated into various access points and systems, offering robust protection without compromising user experience.
Preventing the New Wave of Threats
Whiteswan is at the forefront of prevention in the face of ever-evolving cyber threats. By emphasizing the significance of MFA everywhere, Whiteswan addresses the persistent threat of compromised credentials head-on.
With MFA in place, stolen passwords become insufficient for unauthorized access, significantly reducing the attack surface.
Moreover, Whiteswan’s approach to securing RDP access is a game-changer. It recognizes that RDP is a common culprit in lateral movement by attackers.
By implementing stringent security measures and access controls, Whiteswan helps organizations close this vulnerability, making it exceptionally difficult for cybercriminals to move laterally within the network.
Case Studies and Examples
To illustrate the real-world impact of Whiteswan’s approach, let’s consider a few hypothetical scenarios:
Scenario 1: The Phishing Attempt
Employees fall victim to a sophisticated phishing email that steals their login credentials.
However, thanks to Whiteswan’s MFA Anywhere, the attacker’s attempts to access critical systems are thwarted.
The attacker cannot proceed without the second authentication factor, even with the stolen password. This defense mechanism buys valuable time for the organization’s security team to investigate and neutralize the threat.
Scenario 2: Preventing Lateral Movement
An attacker manages to breach an organization’s network through a vulnerable RDP connection.
However, Whiteswan’s robust RDP security features detect the unauthorized access attempt and immediately block the attacker’s progress.
The lateral movement is halted in its tracks, preventing further compromise of critical systems.
Conclusion
In the relentless battle against cyber threats, organizations must employ a multi-faceted approach to security. Compromised credentials, reduced dwell time, continuous attack activity, and the attractiveness of Active Directory and RDP as targets are just a few of the challenges they face.
However, enterprises can significantly enhance their security posture by emphasizing the importance of MFA everywhere and securing against unsecured RDP access.
Whiteswan’s innovative solutions, particularly its MFA Anywhere feature, empower organizations to address these challenges effectively.
By preventing unauthorized access, reducing the attack surface, and enabling continuous monitoring through comprehensive telemetry data, Whiteswan is leading the way in fortifying enterprise security.
As the threat landscape continues to evolve, organizations prioritizing MFA and ZSP, with solutions like Whiteswan, are better positioned to protect their critical assets and data. In this digital transformation era, proactive security measures are not an option; they are a necessity. It’s time for enterprises to take action and secure their future in an increasingly interconnected world.



