Identity and access management today is rapidly evolving and how organizations work has changed drastically, throwing up unprecedented challenges.
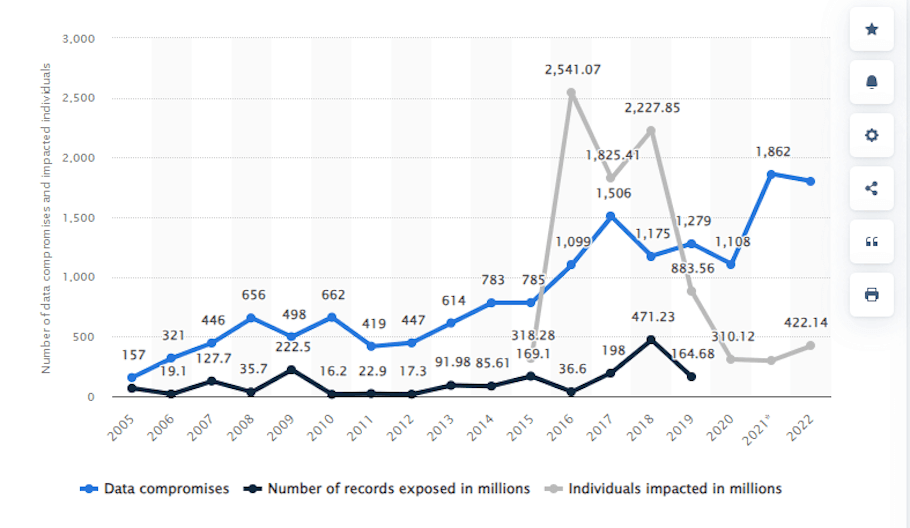
The escalating frequency of data compromises, breaches, leaks, and exposures in 2022, affecting over 422 million individuals in the United States alone (1,802 data compromises in the United States), underscores the urgency for a paradigm shift in security strategies.

The common thread binding these incidents is unauthorized access—a persistent threat that organizations must confront to safeguard sensitive data and maintain the trust of their stakeholders.
Identity and Access Management – Evolution of Endpoint Security
To fortify against advanced threats such as ransomware and zero-day exploits, organizations recognize the imperative to evolve their endpoint security strategies.
While a longstanding practice, reliance on traditional password authentication comes at a cost – prolonged login times, manual processes, and the ever-looming possibility of data breaches when employees manage passwords.
Identity Centric Zero Trust Network Access (ZTNA) is rapidly becoming a transformative factor in identity and access management, surpassing traditional models. Identity Centric ZTNA represents a departure from presumptive trust, introducing a dynamic security posture that aligns with the evolving nature of cyber threats.
As we navigate through the intricacies of Identity Centric ZTNA, we’ll explore its principles, applications, and the role it plays in redefining endpoint security for superior protection.
Understanding Identity Centric ZTNA
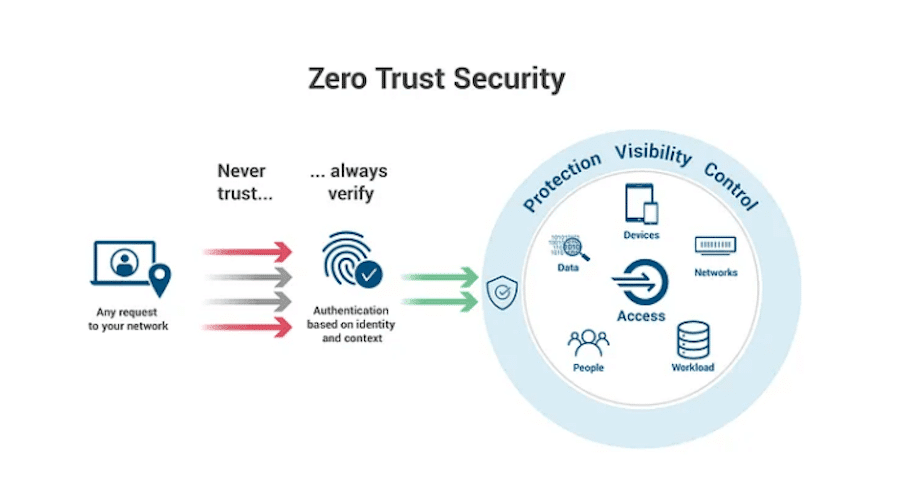
In the evolution of endpoint security, identity centric ZTNA emerges as a beacon of innovation. At its core, ZTNA redefines the approach to secure access by prioritizing user identity, device attributes, and contextual factors. This departure from the traditional reliance on passwords addresses the limitations of static authentication methods.
This paradigm shift aligns seamlessly with the principles of identity and access management, providing a comprehensive solution to enhance overall security.
Transformative Potential of Identity Centric ZTNA

- Continuous Verification: Unlike conventional models, identity centric ZTNA adopts a “never trust, always verify” philosophy. This continuous verification ensures that user identities and device health are consistently validated, mitigating the risk of unauthorized access.
- Adaptive Policies: ZTNA’s adaptive policies intelligently adapt to user context, ensuring a frictionless experience for authorized users while bolstering security through real-time access tailoring.
- Least-Privilege Access: The principle of least privilege is a cornerstone of ZTNA, restricting access to the minimum necessary for users to perform their roles. This granular control minimizes potential attack surfaces and limits the impact of security breaches.
- User-Centric Experience: Adopting adaptive policies ensures a user-friendly experience, reducing friction while maintaining a high level of security.
- Mitigation of Credential Risks: With reduced reliance on passwords, ZTNA minimizes the risks associated with credential-based attacks, providing a more secure access framework.
Applications of Identity Centric ZTNA
In the dynamic and interconnected digital ecosystem, identity centric ZTNA finds diverse applications, addressing security concerns across various fronts:
Secure Remote Access: Identity-centric ZTNA facilitates secure remote access, enabling employees, contractors, and partners to connect to company resources, applications, and data from anywhere. This ensures a seamless yet highly secure workflow regardless of geographical constraints. The implementation of identity and access management principles enhances the overall security posture in remote access scenarios.
Cloud Connectivity: ZTNA extends its protective umbrella to different cloud environments, including AWS, Google Cloud, and Azure. Organizations can leverage ZTNA to control and monitor access to multi-cloud resources, adding an extra layer of security in cloud interactions. This approach aligns with robust identity and access management strategies, ensuring comprehensive protection in cloud connectivity.
Third-Party Vendor Access: Granting secure, controlled access to third-party vendors and suppliers becomes a streamlined process with ZTNA. This ensures that external entities interacting with an organization’s systems, applications, or data adhere to stringent access controls. The incorporation of identity and access management protocols further strengthens the security framework in managing third-party access.
Microservices and Containers: ZTNA secures connections between microservices and containers within distributed applications. This precision in access control ensures that communication is exclusively permitted between authorized services, fortifying the integrity of distributed applications. The integration of identity and access management practices enhances the overall governance and security of microservices and containerized environments.
IoT Device Security: Safeguarding the communication between Internet of Things (IoT) devices and central servers is critical. ZTNA enforces strict access controls, protecting against unauthorized device access and potential data breaches in the IoT ecosystem. The application of identity and access management principles plays a pivotal role in establishing a robust security foundation for IoT device interactions.
Comparative Analysis: Identity Centric ZTNA vs. On-Premises Firewall VPN
Zero Trust Architecture:
- ZTNA: Employs a decentralized, identity centric model, granting access based on user identity, device attributes, and context.
- On-Premises Firewall VPN: Utilizes a centralized model where users connect to a central server before accessing resources.
Access Control:
- ZTNA: Enforces strict access control through micro-segmentation, providing least-privilege access to specific resources.
- On-Premises Firewall VPN: Tends to offer broader access permissions, often requiring users to be on the corporate network before applying access controls.
Security Posture:
- ZTNA: Assumes a “never trust, always verify” approach, continuously validating user identity and device health.
- On-Premises Firewall VPN: Often relies on trust established during initial login, which may not be continuously verified.
User Experience:
- ZTNA: Offers a seamless user experience with adaptive policies, reducing friction while maintaining security.
- On-Premises Firewall VPN: Introduces user friction due to multiple logins and network switches.
Scalability:
- ZTNA: Highly scalable and suitable for modern, dynamic work environments.
- On-Premises Firewall VPN: Becomes complex to manage and scale as organizations grow.
Performance:
- ZTNA: Optimizes network performance by routing traffic intelligently based on user and application needs.
- On-Premises Firewall VPN: Introduces latency due to centralized routing and encryption.
Network Complexity:
- ZTNA: Simplifies network architecture by reducing the attack surface and eliminating the need for complex, perimeter-focused security.
- On-Premises Firewall VPN: This may necessitate complex network configurations and maintenance.
Remote Work Support:
- ZTNA: Well-suited for remote work, offering secure access from anywhere without compromising security.
- On-Premises Firewall VPN: Presents challenges in terms of remote access setup and management.
Zero Trust Principles:
- ZTNA: Adheres to core zero trust principles, ensuring that trust is never assumed and access is continuously monitored.
- On-Premises Firewall VPN: Designed with a different trust model and may not align with zero trust principles.
Cloud Integration:
- ZTNA: Seamlessly integrates with cloud services, offering direct, secure access to cloud resources without needing a VPN.
- On-Premises Firewall VPN: Requires additional configurations for secure cloud access.
Compliance and Auditing:
- ZTNA: Provides robust compliance monitoring and auditing capabilities for better regulatory adherence.
- On-Premises Firewall VPN: Has limited auditing and compliance features, requiring additional solutions.
Adaptation to Modern Threats:
- ZTNA: Designed to adapt to evolving cyber threats, including insider threats, using continuous risk assessment.
- On-Premises Firewall VPN: This may not be as agile in adapting to new threat vectors and may rely on outdated security models.
Remote Device Security:
- ZTNA: Focuses on device health and security posture, allowing or denying access based on these factors.
- On-Premises Firewall VPN: May rely more on user credentials, potentially overlooking device security.
Application Security:
- ZTNA: Provides more granular control over application access and data flows, enhancing application security.
- On-Premises Firewall VPN: Often treats applications as a whole, which can be less secure and efficient.
ZTNA for a Safer Hybrid Workspace
In the contemporary working environment, characterized by a blend of in-office and remote work, the hybrid workspace demands a heightened focus on security. Identity centric ZTNA emerges as a linchpin, contributing to a safer and more resilient work environment through:

- Identity Centric Security: ZTNA revolves around the principle of identity, ensuring that only authenticated and authorized users gain access to critical enterprise resources. This adds a robust layer of security to the authentication process.
- Device Trustworthiness: Continuous monitoring of device health and security posture is a hallmark of ZTNA. This guarantees that only trusted and compliant devices can access enterprise systems, reducing the risk of compromised endpoints.
- Secure Remote Access: With remote work becoming the norm, ZTNA facilitates secure access for remote employees. This ensures employees can connect to corporate resources from any location without compromising network security.
- Reduced Attack Surface: By continuously verifying user identities and the health of connected devices, ZTNA reduces the attack surface. Unnecessary exposure to potential threats is minimized, enhancing overall security.
- Granular Access Control: ZTNA enables organizations to exercise precise control over who can access which applications and data. This ensures that sensitive information remains protected and access is tailored to individual roles and responsibilities.
- Enhanced Compliance: ZTNA helps maintain compliance by enforcing robust access control policies and monitoring user activity for industries with strict regulatory requirements, such as healthcare and finance.
- Resilience and Business Continuity: ZTNA adds to an organization’s resilience by ensuring secure access to critical resources despite unexpected disruptions, such as network outages or disasters.
- Improved User Experience: ZTNA can deliver a seamless user experience by minimizing authentication friction, reducing the need for VPNs, and allowing employees to work from anywhere with ease.
Whiteswan Identity Security: Transforming Enterprise Secure Access
Whiteswan Zero Standing Privileges (ZSP) platform emerges as a catalyst in accelerating the journey toward a secure and resilient Zero-Trust Security Posture. Whiteswan Security, through its innovative services, redefines the way organizations approach secure access, offering the following key benefits:
- Zero Trust Acceleration: Whiteswan Security expedites the adoption of a Zero-Trust Security Posture, reducing the attack surface and safeguarding critical assets.
- Granular Access Control: The platform provides precise control over user and device access to applications and data, ensuring that only authorized entities can access them.
- Resilience and Security: Whiteswan Security enhances the resilience of the security posture by continuously monitoring and verifying user identities and device health.
- Secure Application Access: The platform enables secure access to critical applications, ensuring that the right users and devices can interact with them, safeguarding sensitive data.
- Trusted Data Protection: Whiteswan Security maintains a trusted environment, protecting data from unauthorized access and ensuring data integrity and confidentiality.
Identity centric ZTNA stands as a transformative force in cybersecurity, redefining how organizations approach secure access in an era of evolving threats. By prioritizing user identity, device health, and adaptive policies, ZTNA offers a comprehensive solution to the challenges of unauthorized access and data breaches.
As organizations embrace the principles of ZTNA, particularly with innovative solutions like Whiteswan Identity Security, they not only fortify their security posture but also pave the way for a more agile, user-friendly, and resilient future. The journey toward a secure and adaptive Zero Trust Security Posture becomes not just a necessity but a strategic imperative in safeguarding the digital landscape.
Here, we have explored the intricacies of Identity Centric ZTNA, its applications, benefits, and the pivotal role it plays in securing the hybrid workspace. As the cybersecurity landscape continues to evolve, embracing identity centric security becomes not just a choice but a proactive stance against the ever-evolving threat landscape.



